Here’s a fun assessment you can perform on your home network. I’m running Kali Linux 2018.1 in a virtual machine using VMware Workstation Player. My wireless network adapter is an Alfa AWUS036NHA with a 9dBi omni-directional antenna. Penetration testers may use the Fern Wi-Fi cracker as a security auditing tool to test the security of an organization’s wireless network.
Disclaimer:
The information provided on the cybersecurityman is for educational purposes only. I am in no way responsible for any misuse of the information provided. All the information here is meant to provide the reader with the knowledge to defend against hackers and prevent the attacks discussed here. At no time should any reader attempt to use this information for illegal purposes.
The “Fern Wi-Fi Cracker” tool, from hereon abbreviated as “FWC,” is a security auditing and attack software program provided in the Kali Linux distribution. FWC has the ability to crack and recover WEP, WPS, WPA, and WPA2 keys as well as other wireless attacks (even wired too). As for the details, FWC can perform the following (which I’m pulling straight from the Kali Linux page):
- WEP Cracking with Fragmentation, Chop-Chop, Caffe-Latte, Hirte, ARP Request Replay, or WPS attack
- WPA/WPA2 Cracking with Dictionary or WPS-based attacks
- Automatic saving of key in database on successful crack
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Point MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP, HTTPS, TELNET, and FTP)
Things to Keep in Mind
As you should already know WEP is the weakest form of wireless encryption and it was deprecated way back in 2003 by the Wi-Fi Alliance for its inherent security flaws. According to Wigle.net’s Stat Page, about 7.5 percent of wireless networks are still using WEP, so the chances of running into one of these insecure networks are pretty slim; however, they are still out there. Furthermore, 6.8 percent of wireless networks are using WPA encryption and 61.40 percent are using the most secure wireless encryption available, which is WPA2. This doesn’t mean WPA2 is 100 percent secure, I just mean that it’s the best we have until WPA3 rolls out. The remaining wireless networks are using no encryption (4.88 percent) or their encryption type is unknown (19.72 percent). The bottom line is that there are at least 257,252,723 known WPA2 networks, and that’s likely what you’ll be dealing with.

WiGLE collects a lot of information about wireless networks. You should visit their site and browse around or leave a donation.
Another thing to keep in mind is that since the WPS pin is only 8 digits long, it’s very easy to brute force. Software programs like FWC and Reaver can easily guess the pin. The Wi-Fi Alliance has been urging users to disable WPS on their access points since 2011. Since then, all wireless routers and access points come with WPS disabled by default. Seeing as WPS is so widely disapproved, you likely won’t see WPS either.
Step 1: Set Your Wireless Interface into Monitor Mode
There’s two ways to do this. FWC works with Aircrack-ng, so you can open up a new terminal and type airmon-ng start wlan0 or you can automatically set it into Monitor mode by selecting your wireless interface from the drop-down list in the Select Interface tab on the FWC home screen. Setting your wireless interface into Monitor mode is required for FWC to work.
Step 2: Scan for Access PointsIf you wish, you may double-click on any open area of the FWC home screen to bring up the Access Point Preferences screen. On this screen, you can configure which channels you want FWC to scan. You’re most likely going to want to use channels 1, 6, and 11 (b/g/n networks); however, I recommend just leaving it at its default setting for “All Channels.”
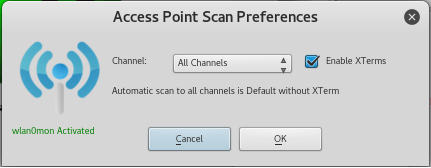
And, if you’d like to, you can enable “XTerms.” This is not required, but it does open up a terminal to display FWC’s scanning of the wireless frequencies. It’s identical to the airodump-ng command. Enabling XTerms allows you to see FWC’s real-time scan for WEP and WPA access points. Click the Scan for Access Points button to begin your scan.
Let this scan run for a little while and observe all of the wireless networks FWC can find for you. It will display the BSSID (MAC address of the AP), power level, beacons, encryption type (WEP/WPA/WPA2), cipher (AES or CCMP), authentication (PSK, MGT, or Enterprise), and the ESSID (which is just the SSID or Network Name). As you can see, there’s plenty of WPA/WPA2 networks, but almost no WEP networks. You should be able to find your home network SSID in the list. That is the network you are allowed to test on.Looking at either the WEP or WPA scan terminal, you should see a separate list at the bottom. Under the “BSSID” column, you’ll see the MAC address of the AP. BSSID stands for “Basic Service Set Identifier,” but that’s not something you need to know. Under the “Station” column, you’ll see the MAC address of devices currently connected to that AP. FWC requires at least one device be connected to an AP for it to work, and you’ll see why that is in a moment.

I’m using a 9dBi antenna, so I’m capturing a crazy amount of networks. You can see some of the devices currently connected to a few APs at the bottom.
Step 3: Choose WEP or WPA
Your home network should be using WPA2, so choose the Wi-Fi WPA button to bring up the Attack Panel window.

If you’re using WEP for some reason, click the Wi-Fi WEP button.
Step 4: Setting up the Attack
In the Attack Panel window, you’ll see a list of networks FWC discovered during the scan. Find your home network in the scan and click on it. After that, you can choose between a “Regular Attack” and a “WPS Attack.” Most likely, you’ve disabled WPS, but you can enable it on your Access Point if want to try the WPS attack out for yourself. If not, choose the Regular Attack option.

Don’t worry that I’ve displayed these networks as they are already publicly displayed on WiGLE’s web site.
FWC uses a default “word list” file filled with common passwords, called common.txt. In my opinion, this file sucks and you should browse online for a more updated file that contains thousands and thousands of passwords. If you have an alternative file to use, then click the Browse button and select it.
Click the Regular Attack box and then from the drop down list, select a device you want to deauth from the network. It doesn’t really matter which one you choose.

Pick one.
Displaying the MAC addresses here isn’t a big deal; after all, MAC addresses are not globally traceable.
Step 5: Attack
Click the Wi-Fi Attack button and follow along with 5 steps. FWC will highlight each step yellow when it’s finished. I did two attacks and de-auhenticated two different devices.
FWC will send a deauthentication (deauth) frame to the device you selected and knock it off your network. It uses the aireplay-ng command to do this. The device will then attempt to re-connect to the network and it’s at that point that FWC captures the 4-way handshake between the device and the access point. After the 4-way handshake is captured, FWC will use the word list file you chose for the brute force attack.If you enabled XTerms, then the terminal windows will open during the attack, showing you the deauth process taking place in the background.
If you have a really strong password, the common.txt file isn’t going to help you. As I mentioned earlier, try a better word list file to test your password strength. Or, you can temporarily set your password to something easily brute forced. If FWC can crack the passphrase, it will be displayed at the bottom. If not, it will suggest updating your word list. If you are using a WPS attack, the 8-digit PIN will also be displayed. This assessment highlights the importance of having strong passwords. Weak passwords can be cracked in under 3 minutes.