When building an app that needs to store and share data from a server, software developers can rely on Google’s Firebase Realtime cloud-hosted database. This Infrastructure as a Service (IaaS) removes serious time constraints by providing app developers with maintenance and support, offline support, and real-time synchronization of data with clients in real-time. And, since Software Development Kits (SDKs) are available for iOS, Android, and JavaScript, it is a very popular option that’s currently serving over 53,000 apps with an easy-to-use back-end development platform.
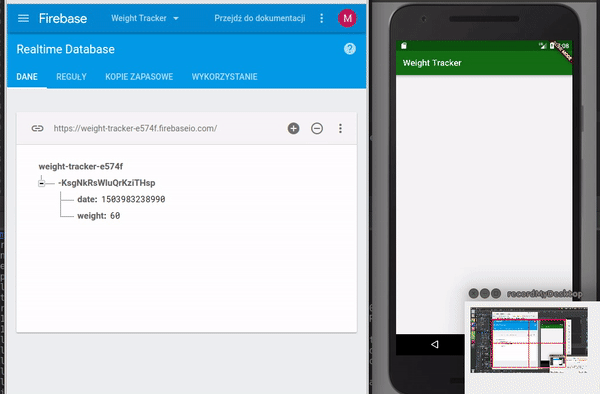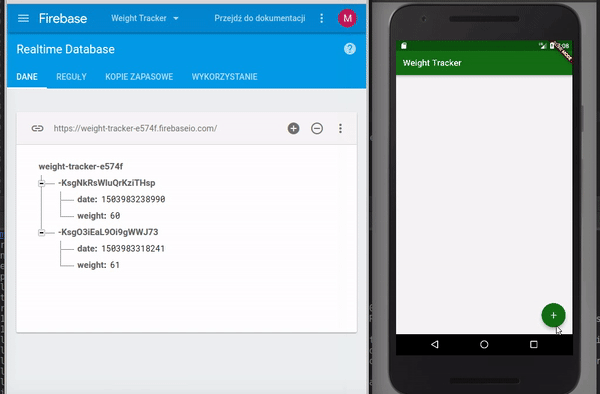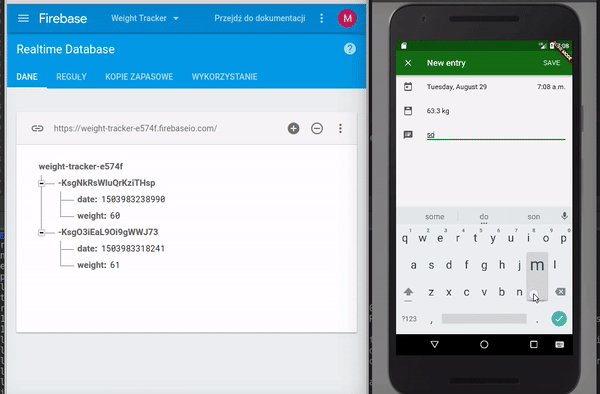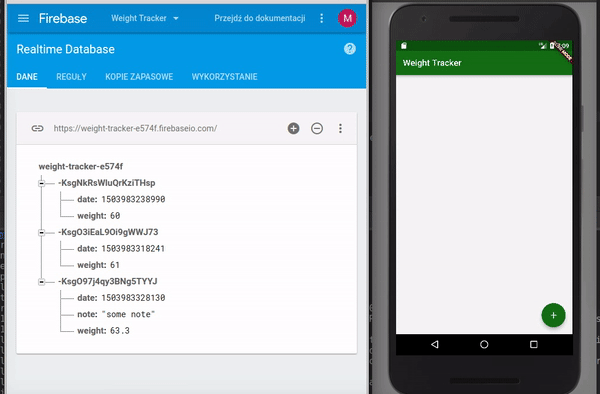
Pushing Weightlist Data to a Firebase Database. Reprinted from “FIREBASE DATABASE IN FLUTTER – WEIGHTTRACKER 3,” by Mszalek, 2017.
However, this week, Appthority mobile security researchers uncovered Firebase databases of thousands of iOS and Android apps, which exposed over 100 million data records, including email addresses, plaintext passwords, user IDs, GPS locations, Personal Health Information (PHI), social media datastore user tokens, and financial records.
The back-end Firebase development platform stores data in JavaScript Object Notation (JSON) format. This is an easy and organized way to store data, mainly because it uses human-readable text that can be accessed in a logical manner. If you’re unfamiliar with JSON, Jason Lengstorf provides a practical example of how JSON works in modern app development.
As far as security goes, Firebase database security rules specify who is authorized to access particular pieces of data. It also comes with authentication, but it’s the responsibility of app developers to enable these security features. According to Appthority’s Mobile Threat team, however, many app developers have failed to require authentication to their Firebase databases, leaving millions of customer sensitive-data exposed to the public.

Vulnerable App. Reprinted from “Thousands of Mobile Apps Expose Their Unprotected Firebase Hosted Databases,” by Mohit, K., 2018.
Firebase also does not secure user data by default and there are no third-party tools available to encrypt this data; therefore, it would be very easy for hackers to access this treasure-trove of sensitive information. Though Google could be partially to blame for not providing these security features, it’s likely more of a mismanagement issue on the developer’s end. App developers should understand that most of these popular platforms are predominantly concerned with ease-of-use rather than security because added security settings commonly remove its smooth functionality. Accordingly, security settings are disabled by default unless app developers choose to use them.
As for more approximate estimates, Appthority states 600 mobile iOS and 2,446 Android apps were exposing 113 gigabytes of sensitive data. Of this data, 2.6 million are plaintext password/username combinations, 4 million are PHI records, 25 million are GPS locations, 50,000 are financial records, and 4.5 million come from Facebook, LinkedIn, Firebase and corporate datastore user tokens. The apps exposing user data come from popular banking, telecom, ride-sharing companies, education, hotels, productivity, postal services, and health/fitness apps, all of which were downloaded more than 620 million times.
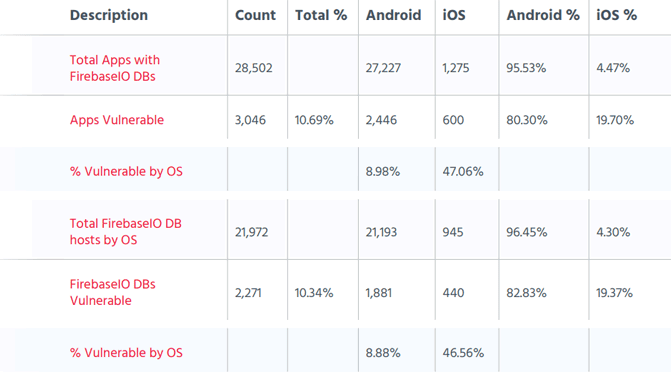
Appthority Report. Reprinted from “Thousands of Mobile Apps Expose Their Unprotected Firebase Hosted Databases,” by Mohit, K., 2018.
Appthority has already notified Google of this security issue before it published its comprehensive report. It also provided a list of affected apps and Firebase database servers. App developers who are affected by this leaky back-end have likely already been notified and patched this security issue.
References
Bacon, M. (2018). Unprotected Firebase Databases Leaked Over 100 Million Records. Appthority. Retrieved from https://www.appthority.com/company/press/media-coverage/unprotected-firebase-databases-leaked-over-100-million-records/
Cimpanu, C. (2018). Thousands of Apps Leak Sensitive Data via Misconfigured Firebase Backends. Bleeping Computer LLC. Retrieved from https://www.bleepingcomputer.com/news/security/thousands-of-apps-leak-sensitive-data-via-misconfigured-firebase-backends/
Kumar, M. (2018). Thousands of Mobile Apps Expose Their Unprotected Firebase Hosted Databases. The Hacker News. Retrieved from https://thehackernews.com/2018/06/mobile-security-firebase-hosting.html
Mszalek. (2017). FIREBASE DATABASE IN FLUTTER – WEIGHTTRACKER 3. Retrieved from https://marcinszalek.pl/flutter/firebase-database-flutter-weighttracker/