In this tutorial, I’m using BurpSuite to grab cookie information from a user and feed it into an SQL injection attack using sqlmap. To perform this test attack, I’m using the Damn Vulnerable Web App (DVWA) as a SQL injection vulnerable web site/database. This is a free application you can download for testing. As a prerequisite, the reader should have at least a basic understanding of SQL statements and database management systems.
Burp Suite
Interception proxies, like Burp Suite, are great for improving security because they provide extraordinary insight into user browsing behavior since they serve as an intermediary devices between the user and a requested resource, such as a Web page hosted by a Web server. However, Burp Suite is more than just a proxy. It’s also used to analyze web applications for vulnerabilities. But, when used in Proxy mode, Burp Suite provides an easy-to-use GUI that enables the user to inspect network traffic before either forwarding it or dropping it.

I’m using the Burp Suite Community Edition version 1.7.36, which comes pre-installed in Kali Linux.
Sqlmap
Sqlmap is an automatic SQL injection and database takeover tool that comes pre-installed in Kali Linux. It specializes in detecting and exploiting SQL injection flaws of database servers. The current version at the time of this writing is version 1.2.9 and it provides full support for popular SQL database management systems, including MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, HSQLDB, and Informix. It comes with a niche of features, including support for boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries, and out-of-band SQL injection techniques. Since sqlmap supports these various attacks, users can expect to enumerate database users, password hashes, privileges, roles, databases, tables, columns, and any other helpful information that will be useful during a penetration test. Sqlmap also detects the hash-type of hashed passwords and will crack them using a dictionary attack.
If you do not have sqlmap, you can download it by cloning the Git repository: git clone –depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev. Once installed and updated, view the various options sqlmap has to offer by executing the sqlmap –help command in a new terminal.



Review the provided options that sqlmap provides. The “Enumeration” section will become particularly important in later steps.
Step 1: Set Up Proxy Configurations
For FireFox, navigate to Settings>Preferences and then under the Network Proxy section, click “Settings…” The Connection Settings dialog box should then open.
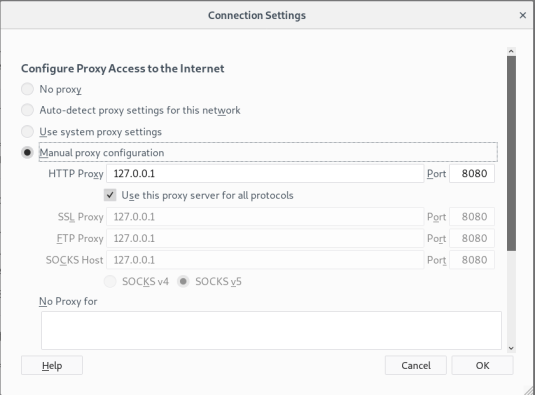
Click on the Manual proxy configuration option and note the preceding output. For my proxy, I’m using the local host on 127.0.0.1 on port 8080 (this is because DVWA runs on my local host). Under the Proxy and Options tab for Burp Suite, I’m using the same exact settings. Now that both theFireFox and Burp Suite proxy settings are configured, FireFox should use Burp Suite as a proxy when using DVWA. Note: Make sure that the No Proxy for section is empty.

Now that a proxy connection has been established, Burp Suite will intercept all network traffic on the local host on port 8080.
Step 2: Steal Cookie Information
We need cookie and session identifiers to use sqlmap in Step 4 and we can obtain information using Burp Suite. Since Burp Suite is acting as a proxy, FireFox will not be able to request any information from the Web server until we forward it in Burp Suite. If, for example, I type the User ID “5” into DVWA and click Submit, nothing happens. This is because Burp Suite has intercepted this GET request to /DVWA/vulnerabilities/sql_blind/. I will not be able to Submit this information until I click the Forward option in Burp Suite.

I can further examine this GET request in Burp Suite under the Proxy and Intercept tabs in several different formats. The formats are different, but the information is all the same. I’ve highlighted the cookie information because I will feed that to sqlmap for the SQL injection attack in Step 4.
Step 3: Copy Information in to a Text FileUsing Burp Suite, I can copy the URL and the cookie information I’ve obtained and temporarily store it in to a text file.

This step is not mandatory, but it makes the following steps a little easier so that I can just simply copy & paste.

Step 4: Scan the Target for Vulnerabilities
Execute the command, sqlmap -u “http://localhost/DVWA/vulnerabilities/sqli_blind/?id=5&Submit=Submit#” –cookie=”security=low; PHPSESSID=2v9td3fa0ou5o40np0f6mbg2vd” in a new terminal window. The -u option is the URL and the –cookie option specifies the cookie and session identifiers I intercepted in Step 2. We can see in the following output where I’ve highlighted a few important notes. Sqlmap will immediately connect to the target URL and begin testing for vulnerabilities. It confirms that the $id (User ID) variable is dynamic. This means that the variable contains user-supplied data that can also be modified with additional SQL statements to provide additional information in the database.
We also see “testing AND boolean-based blind – WHERE or HAVING clause.” What does that mean? This is where knowing SQL really helps. The WHERE clause is an optional clause used in SQL statements, usually used with the SELECT and FROM clauses. The WHERE clause acts as a filter on the rows of the result set produced by the FROM clause. It extracts only those records that fulfill a specified criterion. The WHERE clause mainly depends on a condition that evaluates as either true, false, or unknown. For example, a malicious user could submit the query, “5 OR 1=1”. Since the “1=1” condition is always TRUE, the malicious user can access all the user’s information.

Sqlmap then asks, “It looks like the back-end DBMS is “MySQL.” Do you want to skip test payloads specific for other DBMSes?” Since I know DVWA is using a MySQL database, I chose “No.” Sqlmap will then continue to scan for additional vulnerabilities against the database. Note how it determines that the table in the database I’m targeting is using two columns. I’m then asked, “Injection not exploitable with NULL values. Do you want to try with a random integer value for option ‘–union-char’?” If you’re interested in finding a union-based SQL injection that exploits the the UNION sql operator, then enter “Yes.” Otherwise, enter “No.”

You may or may not be asked similar questions throughout the scanning process. It’s up to you whether or not you want to focus on a single, specific vulnerability or identify as many vulnerabilities as you can. I would suggest finding as many vulnerabilities as you can.

Here are the vulnerabilities I found in the DVWA. As we can see in the following output, the GET parameter “id” is vulnerable to a boolean-based blind, AND/OR time-based blind, and error-based vulnerabilities.

We also get to see additional information, including the fact that the target is running a Linux Debian distribution web server with Apache version 2.4.34. We also see that it’s using MySQL as the database management system. All this information is stored in /root/.sqlmap/output/localhost for further review.
Step 5: Reveal the Database Names
To find the names of the databases, we use a similar command as earlier: sqlmap -u “http://localhost/DVWA/vulnerabilities/sqli_blind/?id=5&Submit=Submit#” –cookie=”security=low; PHPSESSID=2v9td3fa0ou5o40np0f6mbg2vd” –dbs. The only difference is that we’ve appended the –dbs option to the end.

The output is also similar, but this time, we get two database names: “dvwa” and “information schema.” I’m only interested in “dvwa.”
Step 6: Reveal dvwa tables
To find the tables inside the dvwa database, use the sqlmap -u “http://localhost/DVWA/vulnerabilities/sqli_blind/?id=5&Submit=Submit#” –cookie=”security=low; PHPSESSID=2v9td3fa0ou5o40np0f6mbg2vd” -D dvwa –tables command. If you haven’t noticed yet, we’re using the same command over and over again, but just appending different options. The -D specifies the name of the database to search for and the –tables option tells sqlmap to uncover the tables inside that database.

Sqlmap returns 2 tables inside the dvwa database: “guestbook” and “users.” Out of the two tables, I’m interested in “users.”
Step 7: Reveal Users Table
Now, I want to see the columns that were created for the “users” table inside the dvwa database. We can do that with the command: sqlmap -u “http://localhost/DVWA/vulnerabilities/sqli_blind/?id=5&Submit=Submit#” –cookie=”security=low; PHPSESSID=2v9td3fa0ou5o40np0f6mbg2vd” -T users –columns. Again, this is the same command, but we’re appending different options. This time, the -T option specifies the table I want to enumerate and the –columns option tells sqlmap to list out the columns for that table.

Sqlmap retrieves a total of 8 columns (and their types) inside the users table. The type field isn’t exactly important, it just states the type and character length. For example, the user_id can be any integer between 1 and 6. I’m only interested in two columns: “user” and “password.”
Step 8: Dump Usernames and Passwords and Crack Hashes
To reveal the usernames and passwords in the “user” and “password” columns, execute the sqlmap -u “http://localhost/DVWA/vulnerabilities/sqli_blind/?id=5&Submit=Submit#” –cookie=”security=low; PHPSESSID=2v9td3fa0ou5o40np0f6mbg2vd” -C user,password –dump command. The -C option specifies the columns we want to use (user and password) and the –dump option dumps the table entries in the output.

Sqlmap quickly retrieves the table entries for the user and password columns in the users table inside the dvwa database. We get the usernames and the MD5 hashes of the passwords. Sqlmap then asks “do you want to store hashes to a temporary file for eventual further processing with other tools?” This is a great option, but I chose “No” because I know the hashes are extremely easy to crack. I’m then asked, “do you want to crack them via a dictionary-based attack?” Sqlmap comes with several word lists stored in /usr/share/sqlmap/txt/.

I chose the default word list to crack the hashes.


Sqlmap then uses a dictionary-based password cracking attack to crack the hashes of the passwords.
- Username 1337 = charley
- Username admin = password
- Username gordonb = abc123
- Username pablo = letmein
- Username smithy = password

