Penetration testing and security analysis is an integral aspect of cybersecurity. The ability to master some of these tools is certainly indispensable. Penetration testers and other cybersecurity professionals use these tools everyday to examine the security posture of their networks. All of these tools are free to download; however, whether you can use them or not depends on your operating system and network adapter (and your level of patience). Because these tools are freeware and generally opensource, hackers can easily obtain these tools and master them for more nefarious reasons.
The information provided on the cybersecurityman is for educational purposes only. I am in no way responsible for any misuse of the information provided. All the information here is meant to provide the reader with the knowledge to defend against hackers and prevent the attacks discussed here. At no time should any reader attempt to use this information for illegal purposes.
Aircrack-ng

My favorite Wi-Fi hacking tool to use is “Aircrack-ng.” Aircrack-ng is a complete suite of tools to assess Wi-Fi network security. Aircrack-ng runs under Linux, FreeBSD, OS X, OpenBSD, and Windows operating systems. Personally, I have Aircrack-ng installed on my Windows OS and my Kali Linux VM and it works great so long as you have a wireless network adapter that supports monitor mode and packet injection.
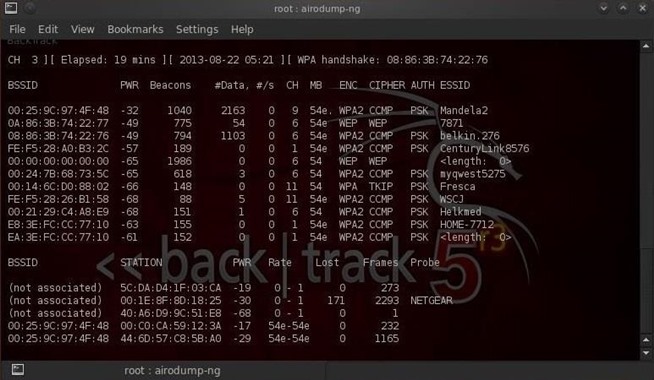
Some of the cool features of Aircack-ng are WEP key cracking using either FMS attacks, PTW attacks, or cafe latte attacks. Unfortunately, this feature is pointless on modern networks since WEP has been deprecated by the Wi-Fi folks. If you’re using WEP on your wireless network, you need to get with the times because you’re about 10 years behind. On the other hand, Aircrack-ng can crack modern day wireless encryption standards, like WPA/WPA2-PSK using dictionary attacks.

Of course, with any Wi-Fi hacking tool, Aircrack-ng gives you the ability to monitor wireless traffic, capture it, and export it for analysis. But, the really nice thing about Aircrack-ng, where most tools fail to deliver, is the ability to perform packet injection. With packet injection, you can attack wireless clients, create fake access points, and perform replay attacks (as we saw with the recent KRACK attacks that cracked WPA2). In this video, I use Aircrack-ng to create an Evil Twin. An Evil Twin is a clone of a wireless access point.
Wireshark

What’s Wi-Fi hacking without “Wireshark?” Wireshark is a free, opensource network protocol analyzer and it runs on Linux, OS X, FreeBSD, and Windows operating systems. Wireshark captures wired and wireless packets and displays them in a very detailed, GUI format. Most network techs and cybersecurity professionals use Wireshark for troubleshooting network problems, observing traffic, examine security problems, and debugging protocol information; however, most hackers use Wireshark as a way to “sniff” open Wi-Fi networks for sensitive information.
Wireshark uses either libpcap or WinPcap to capture packet data. The “lib” stands for “library; the “p” stands for “promiscuous” or “packet;” and the “cap” stands for “capture.” Together, “libpcap” stands for “promiscuous library capture.” Packet capture consists of an application programming interface (API) for capturing network traffic. Libpcap provides implementation-independent access to the underlying packet capture facility provided by the operating system. So, pretty much, libpcap is what we use to grab packets right as they come off of the network interface adapter. UNIX/Linux platforms come with libpcap. If you’re using a Windows OS, you can download WinPcap instead.
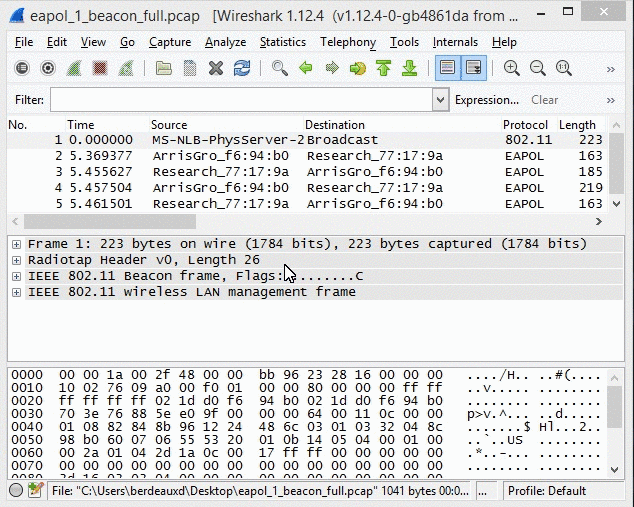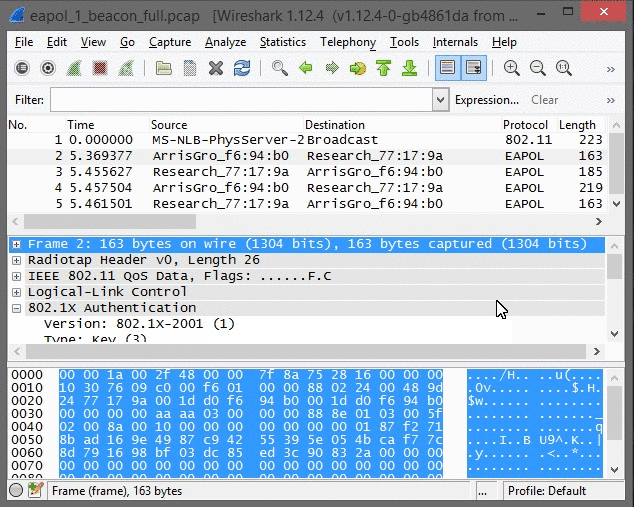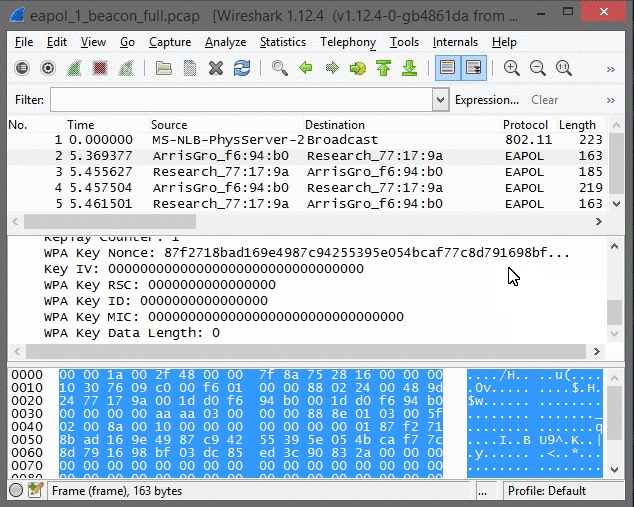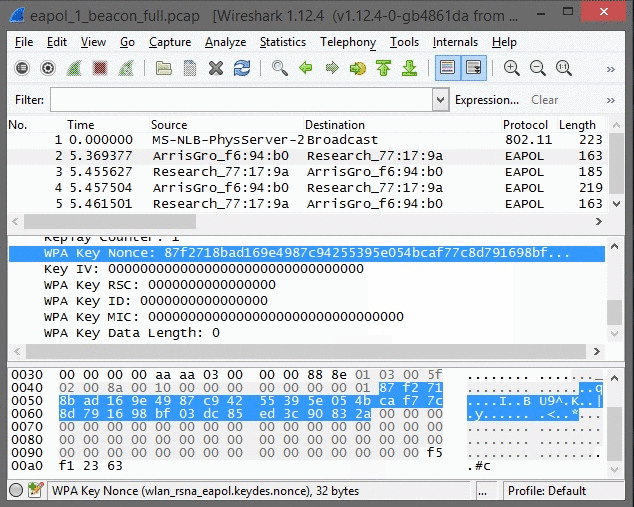
Wireshark has three panes to view: the Packet List pane at the top window; the Packet Details pane in the middle window; and the Packet Bytes pane at the bottom window. Each one of these panes provide an extraordinary amount of detail for each packet.
Cain & Abel

The MS Windows password recovery tool, “Cain & Abel,” is also a suite of useful tools with a list of features that go on and on. With Cain & Abel, you can recover passwords using network password sniffing, password hash cracking, uncovering cached passwords, dictionary attacks, brute force attacks, and cryptanalysis attacks using Rainbow tables. Cain & Abel possess the ability to crack a lot of different hashes, ranging from the weaker MD2/4/5 hashes to the more modern SHA-2 hashes.
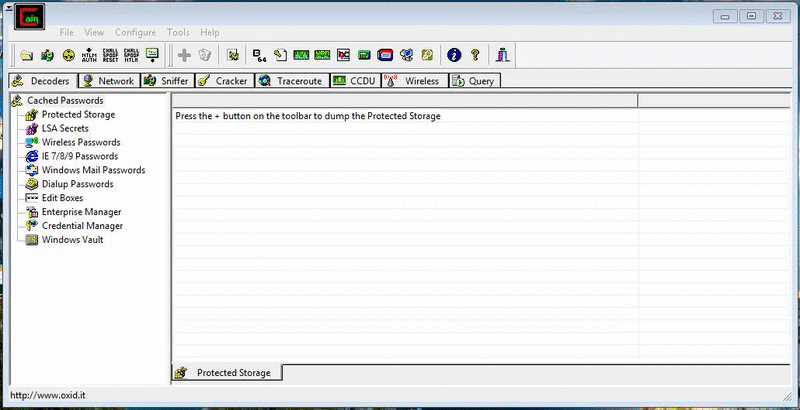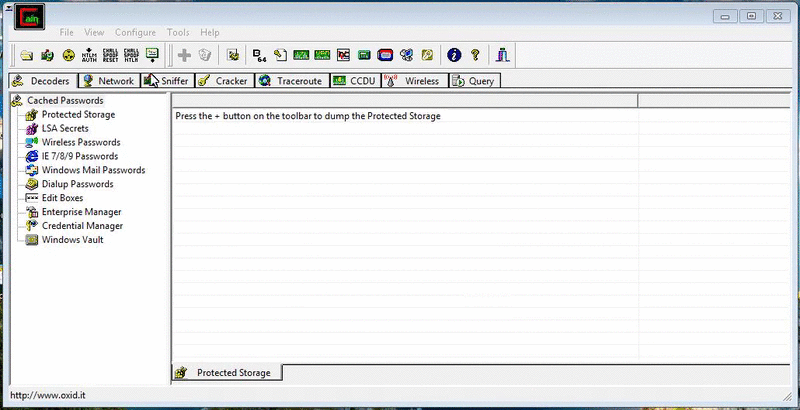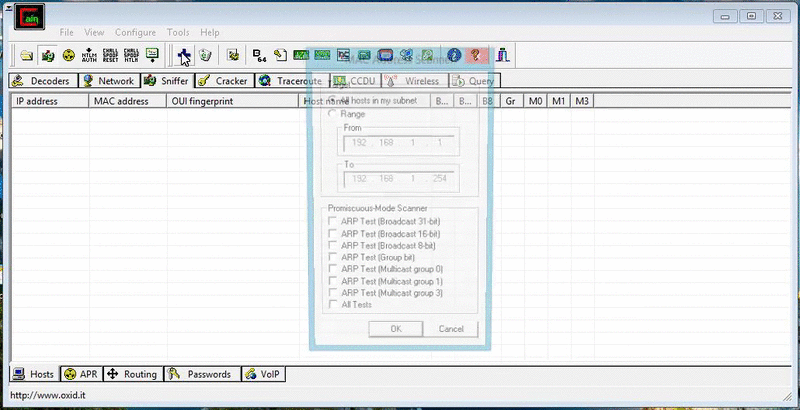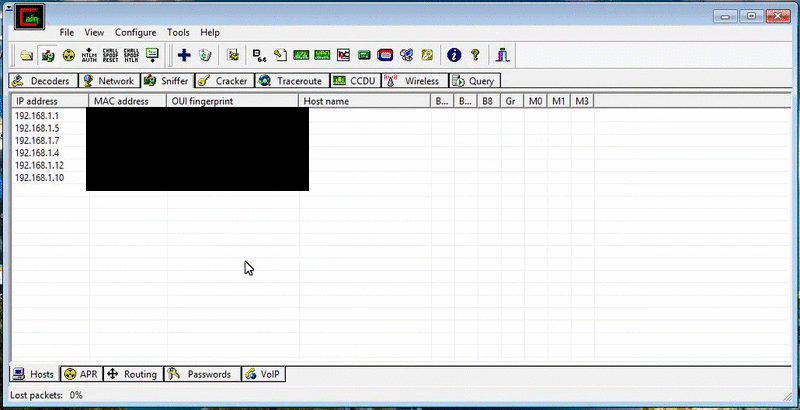
Cain & Abel also possesses a MAC address scanner that scans for devices on the network. It should be considered a MAC address to IP address resolver since it also displays the devices’ IP addresses too. With the MAC and IP address pairs captured, Cain & Abel can be used to perform Man-in-the-Middle (MitM) attacks via ARP poisoning. You can watch me perform a MitM using Cain & Abel here.
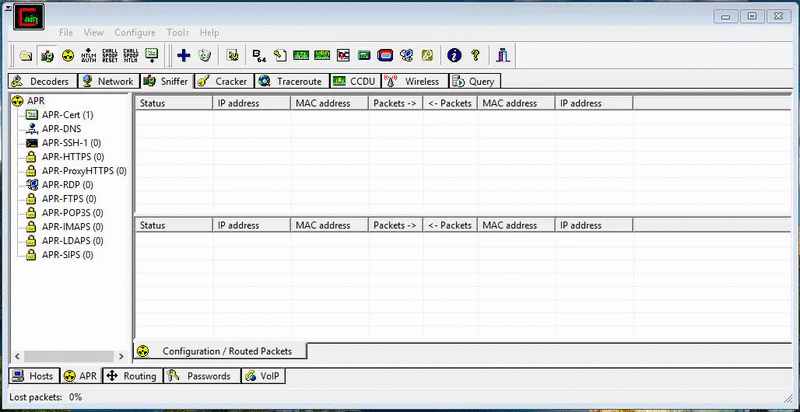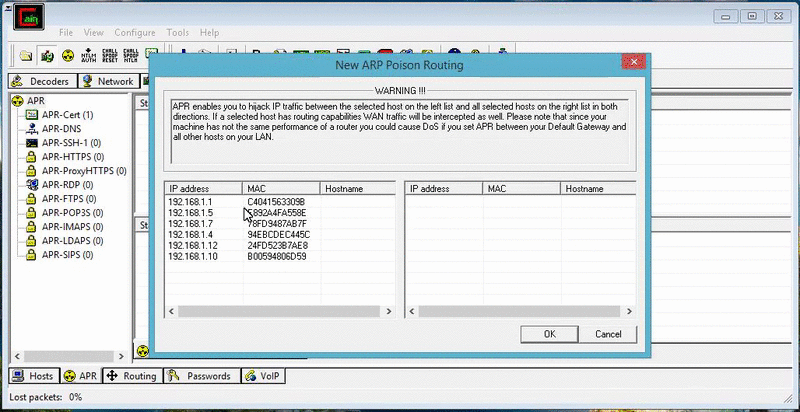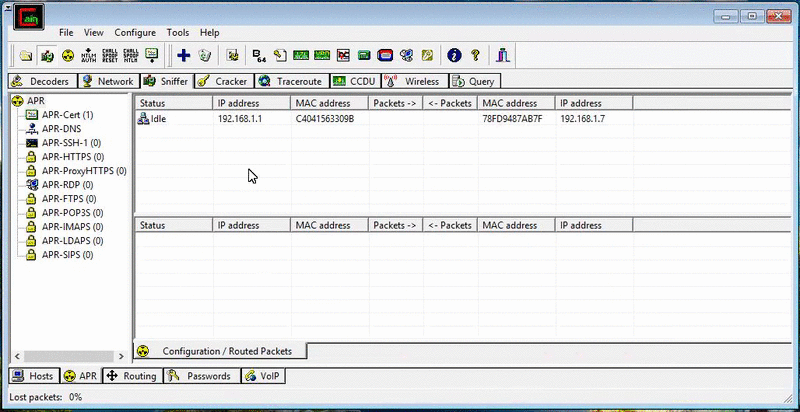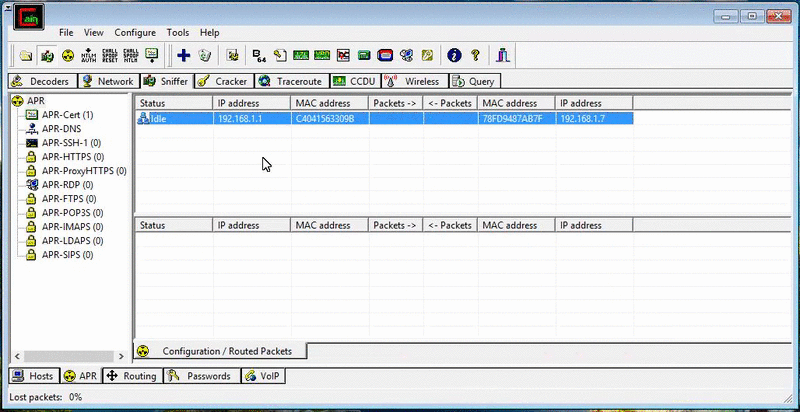
With a MitM attack, hackers can steal passwords, inject spoofed information, and decrypt traffic of the victims affected. Overall, Cain & Abel is an extremely useful tool and, since there’s so many things to do with the software, I’m still discovering new things as I go.
Cain & Abel even has a wireless network scanner to identify and reveal seen and past-seen wireless networks, similar to Aircrack-ng’s Airodump-ng. feature.Ettercap

“Ettercap” is primarily used by penetration testers and hackers for MitM attacks. It can run on Linux, OS X, Solaris, FreeBSD, and Windows operating systems. Just like Cain & Abel, Ettercap uses ARP poisoning to initiate MitM attacks.
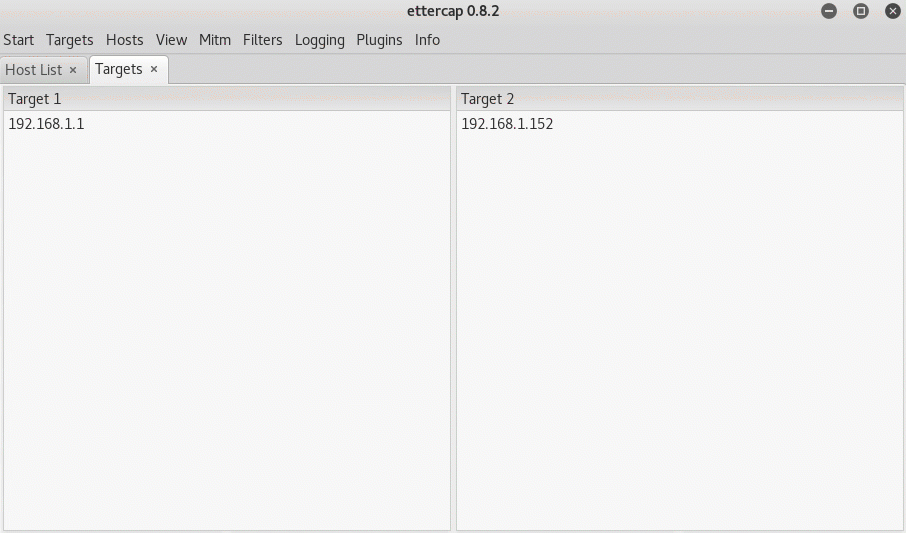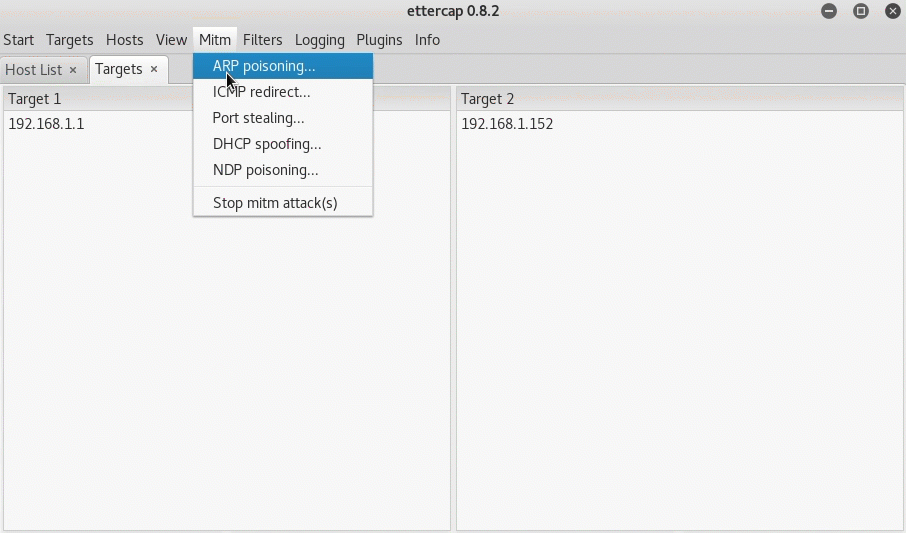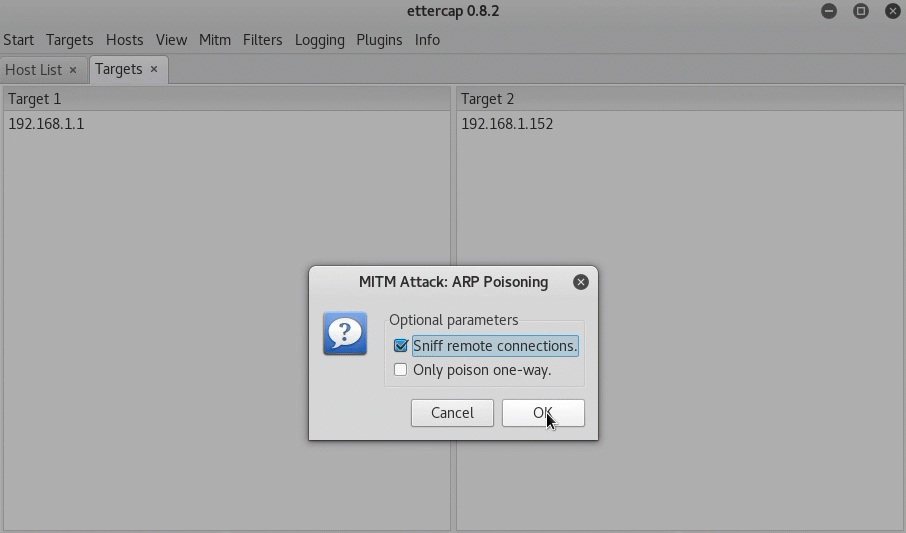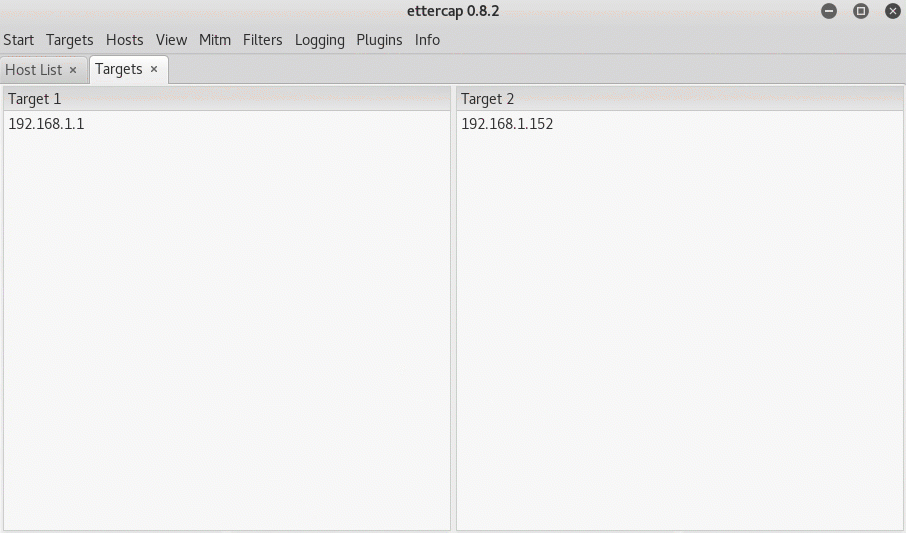
What I like about Ettercap is its ease-of-use. You don’t have to be an expert to understand what to do. Once the MitM attack is initiated, Ettercap will collect passwords entered by the victim over HTTP, FTP, SSH, Telnet, IMAP4, SNMP, and much more. Hackers like to use Ettercap in combination with the SSLstrip tool to decrpyt HTTPS traffic; however, this has become uncommon these days as more and more Web browsers protect against it.
Angry IP Scanner

The “Angry IP Scanner” is an easy-to-use network scanner that identifies the active and non-active IP addresses of devices on the network. It does this though ICMP echo pinging or UDP packet pinging. In some cases, the Angry IP scanner can resolve MAC addresses and host names of the devices.
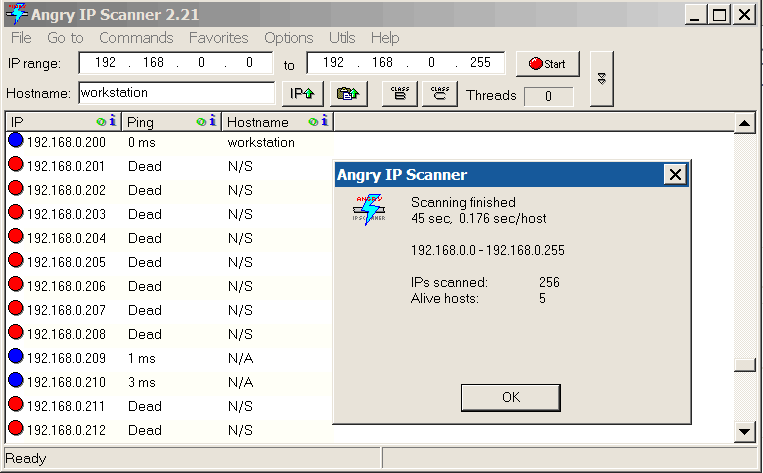
The Angry IP scanner can also port scan devices, revealing which ports are open. From a security standpoint, this is a great feature to have because it notifies security administrators of an open port that should be closed to prevent hackers from exploiting a known or unknown vulnerability.
Nmap

Speaking of port scanning, “Nmap” is my favorite port scanner. Nmap can be used to discover hosts on the network, probe them, reveal open ports and services, and identify operating systems and the version of that operating system. Typically, Nmap is used for auditing, identifying open ports, network mapping, network inventory, and finding or exploiting vulnerabilities by penetration testers. You can use either Nmap’s GUI (Zenmap) or its command line interface, as depicted below.
I worked with Nmap while in graduate school. Our assignment was to discover the open ports and services of the hosts on the network. Additionally, we had to discover the operating system and the version. When Nmap wouldn’t cooperate, we had to experiment using different scanning methods and command options to find the answer. All of the different scanning methods can be found in the user manual. I prefer Zenmap over the command line interface because, number one, it’s just end-user friendly. And, number two, it has this nice topology map feature, as you can see above.Fern Wi-Fi Cracker

As one of the software packages available in Kali Linux, “Fern Wi-Fi Cracker” is a great penetration testing tool that can crack WEP/WPA/WPS keys. Fern Wi-Fi Cracker can crack WEP keys using Fragmentation, Chop-Chop, Cafe-Latte attacks, Hirte, ARP Request Replay attacks, and WPS attacks. WPA/WPA-PSK keys can be cracked using dictionary or WPS attacks.
Fern Wi-Fi Cracker also has a lot of other cool features, like Access Point MAC address geo-location, brute force attacks, and session hijacking attacks.
Just keep practicing, and you’ll grasp how easy it is to use Fern Wi-Fi Cracker.
Ghost Phisher

“Ghost Phisher” is another reputable Kali Linux Wi-Fi hacking tool. With Ghost Phisher, you can emulate a wireless Access Point (AP), just like with Aircrack-ng (except Ghost Phisher makes it super easy to do). The best part about Ghost Phisher is it comes with built-in DNS and DHCP server capabilities. That way, when a user associates with the AP you created, they can be provided Internet access since the DHCP feature leases this user an IP address and the DNS feature allows them to access Web pages (although you’ll need to modify some of the files in /etc folder).
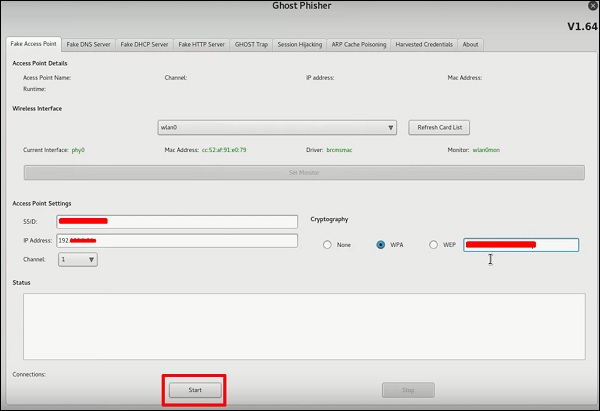
Ghost Phisher can also act as a fake HTTP server that clones the Web page of your choosing and runs it on an assigned IP address. The most common method I see are people cloning the Facebook login page. If attackers can somehow direct a victim to this fake page being cloned by Ghost Phisher, it’s possible the victim will enter their Facebook credentials in order to login. If they do, their credentials will appear in the “Harvested Credentials” tab. 
Ghost Phisher certainly makes hacking a lot more easier for attackers.
Kismet

Kismet is a wireless network detector that will list out the wireless networks your network adapter can detect. Pop on a bigger antenna and you can extend the range even farther. Kismet will also tell you the BSSID of the AP, the SSID of the wireless network, the encryption type (WEP/WPA/WPA2/no encryption), the channel the AP is broadcasting on, the number of packets going into and out of the network, and it will reveal the client MAC addresses connected to that network. Sounds like a lot of useful information, right?
You might be thinking that if you disable SSID broadcasting on your wireless AP that you will be able to prevent Kismet from finding your AP. Unfortunately for you, disabling SSID broadcast is is called, “security through obscurity.” Even if you choose to hide your AP, Kismet will still find it.
